
Contact us
To learn more about Personik opportunities for your team.
Security
of corporate chatbots
of corporate chatbots
Personik creators tell how our platform protects your data
Despite all the advantages, sometimes modern companies hesitate to implement chatbots into their workflow. The concerns are mostly associated with the risks of corporate data breach: by gaining access to the chatbot, hackers can potentially collect sensitive data or employees’ personal records.
However, well-designed protection minimizes such risks. In this article we will answer the most common questions related to the security of chatbots.
However, well-designed protection minimizes such risks. In this article we will answer the most common questions related to the security of chatbots.
Where we store employee data
The main goal of our platform is to make the interaction between HR specialists and employees convenient by automating HR processes. Such automation is most efficient when integrated with the company’s information system which stores employee data.
The work with Personik begins with creating a list of employees: it can be imported from the company’s information system or added manually. When you add a new employee, their basic details (name, phone number, email etc.) are stored in a secured database of the Personik platform.
All records of employee’s contract, sick leaves, past and planned vacations and other relations between the employee and the company are not copied to the Personik platform and remain only in the company’s information system.
From the information system to the employee's messenger: what happens to data when using the bot
If an employee wants to get some personal information (for example, the number of vacation days left in the current year) and sends a request using the bot, the platform checks if they have access to this type of information. This step is called user authorization. Having received a positive answer, Personik contacts the company’s information system through secure channels and requests information.
The next step to ensure the safety of the process is carried out by the company’s information system. It checks the status of the employee (whether they work in the company and have the rights to receive the requested information), implementing the principle of “defense in depth” — protection at every level.
If all the conditions are met, the company’s information system transmits the requested details back to the Personik platform through the same secure channels. Personik records the event of a request and the event of a response of the information system, but the data itself is not logged.
In order to deliver the data into the employee’s messenger, Personik sends it via a secure protocol to the messenger servers. The companies that develop messengers are also fighting to keep the users’ data safe. For example, Viber claims that data passes through servers in encrypted form and is not stored, and Telegram both stores and transmits encrypted data.
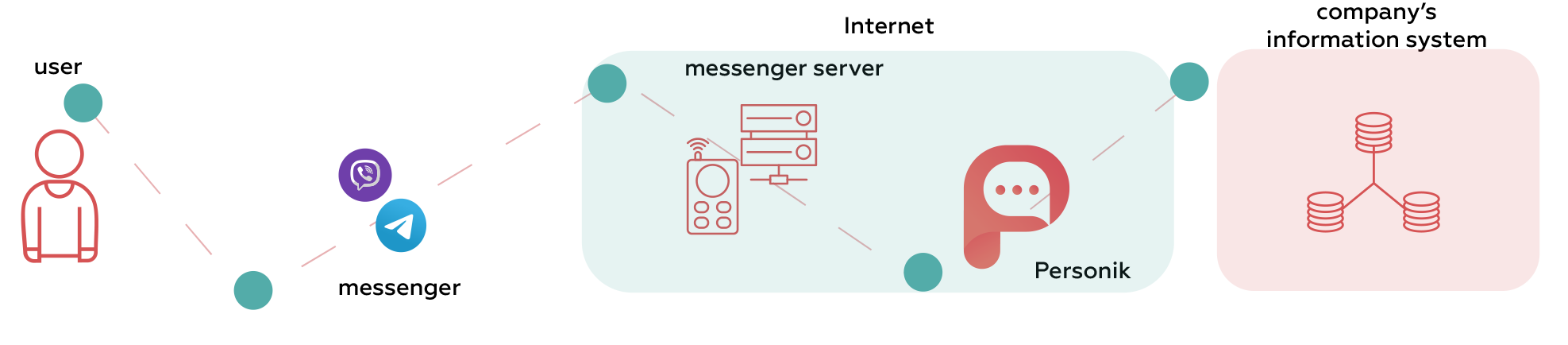
Then the messenger servers send information to the employee. The messenger provides its own unique secure protocol for transferring data between the server and the user’s device.
Thus, to fulfill a request by an employee, the data goes from the company’s information system to the Personik platform, gets to the messenger servers and then to the messaging application installed by the employee.
Thus, to fulfill a request by an employee, the data goes from the company’s information system to the Personik platform, gets to the messenger servers and then to the messaging application installed by the employee.
How do we protect sensitive data?
Sensitive data (for example, financial details) doesn’t go beyond the Personik platform and isn’t transmitted to messengers. It follows a similar path from the information system to the user, but it’s “wrapped” in a file that is temporarily stored on the platform or on the company’s internal servers in a secure perimeter network. As a result, when requesting sensitive data, the employee receives a link to the data file, but not the data itself.
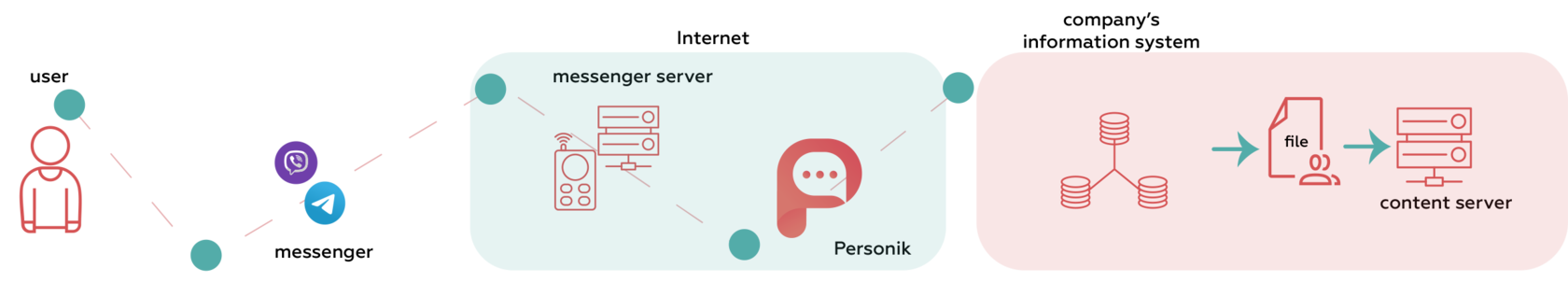
By clicking on the link, the user receives this file directly from the company’s server. The link is available for a limited time and a limited number of downloads. After the expiration of the lifetime, the link and the data file itself are deleted. In addition, we provide the ability to protect the links via two-step authentication, which is implemented by sending a one-time password to the user before getting access to the information.
What we do to provide additional security
We are constantly working to ensure that the code of the platform is completely secure. Our chatbot scripts are designed to prevent intruders from accessing corporate information.
Before working with a new customer, we always check the security of servers and network infrastructure, and build a threat model for all client solutions. It includes threats to the infrastructure and threats to the user. Before launching a chatbot, we also test the bot compliance with the company’s information security requirements.
Three reasons why using Personik is safe
- We store only basic dataBasic employee data is stored in the secure Personik database. Other information is not duplicated on our platform and remains only in the integrated information system of the company.
- We reliably protect the transmission of sensitive dataSensitive data is not transmitted to a messenger and is available to employees only through secure links which lead to the company’s servers. They have a limited lifetime, after which the data files are deleted.
- We always check the platform source code, customer infrastructure and the bot itselfBefore working with a new customer, we build a threat model for the infrastructure and the user, and test the bot for compliance with information security requirements.
Let us know, how we can help!
Kate
Platform Architect
Edward
Software craftsman
Alex
Founder and CEO
Alexander
Master of Operations
Share the article in your favorite network:

